Unlock Rapid Air-Gapped Recovery
The Zerto Cyber Resilience Vault uses ultra-secure zero trust architecture to protect your data and thwart ransomware
Building a Cyber Resilience Vault
Learn how an isolated data vault can help you detect and recover from ransomware using true air gaps, data immutability, and the power of the Zerto journal.
Ransomware Resilience Requires a Recovery Vault
The next evolution of data protection requires ironclad cyber vaults as a key part of any organization’s ransomware resilience strategy. Cyber insurance policies, local and federal regulatory bodies, and industry associations—including Sheltered Harbor for financial institutions—are increasingly requiring fully separated data vaults that cannot be infected by ransomware. These options of last resort are critical during large-scale ransomware attacks.
The Zerto Cyber Resilience Vault meets these needs to enable enterprises to protect, detect, respond, and recover from ransomware. The Zerto vault leverages the unique strengths of Zerto replication and the Zerto journal, combined with industry-leading hardware from HPE, to deliver rapid air-gapped recovery unlike anything else on the market.
Introducing Zerto Cyber Resilience Vault
Experience the best of HPE hardware and software in one powerful solution for ransomware resilience. Zerto, a Hewlett Packard Enterprise company, enables rapid air-gapped recovery through the Cyber Resilience Vault so you can radically reduce data loss and downtime—and without paying any ransoms.
To exit, click outside the image
Introduction to Zerto Cyber Resilience Vault Video (43 sec)

Replicate and Detect
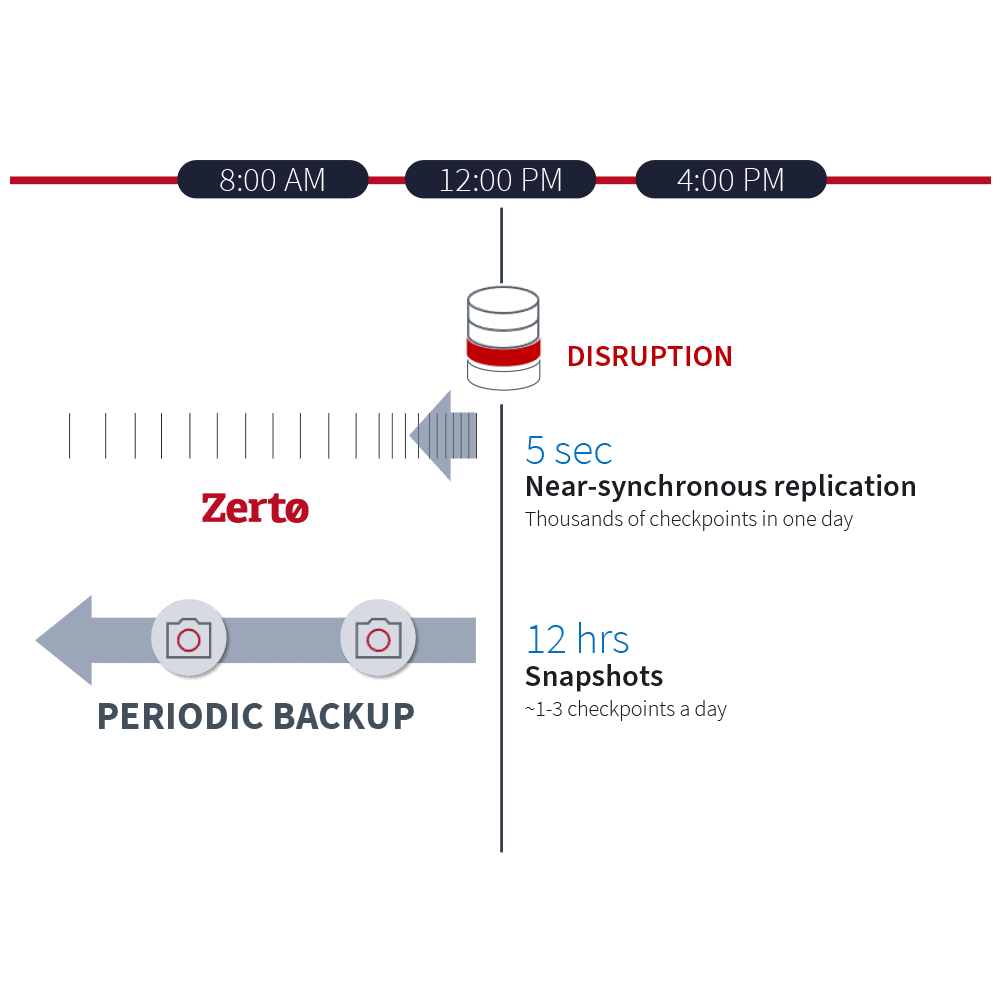
Zerto’s streaming near-synchronous data replication protects every production write in real-time and immediately detects and alerts on any suspicious anomalies. No other data protection solution can offer this type of early warning system for ransomware encryption.
Hypervisor-Based Replication
Real-Time Ransomware Detection
Isolate and Lock
The separated Cyber Resilience Vault is physically air-gapped and stores immutable data copies on secure, high-performance, FIPS-validated hardware.
The isolated vault, or clean room, uses zero trust architecture and has no access to the internet or production network. Since there is no centralized control plane, the vault does not have an exposed management port and does not have any single point of compromise or failure.
Zerto Cyber Resilience Vault Overview
Understanding the Zerto Cyber Resilience Vault
Test and Recover
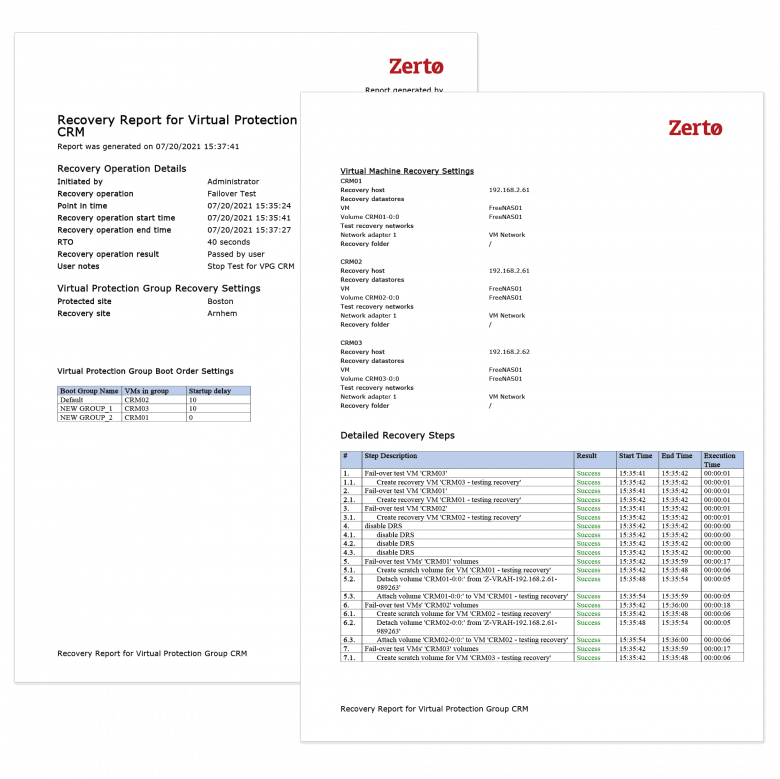
With Zerto, you can carry out orchestrated and automated disaster recovery testing at any time, without production impact, to be confident in your recovery process.
If the need arises, use Zerto to easily identify clean restore points and then quickly recover entire multi-VM apps onto high-performance storage—all while maintaining cross-VM consistency, even with 1000s of VMs.
Zerto’s industry-leading recovery orchestration and automation ensures you can quickly resume operations even if production infrastructure is still compromised or unavailable because of forensic analyses.
Recovery is the Cornerstone of Ransomware Resilience
Key Benefits of Zerto Cyber Resilience Vault
What's Next?
Have a question about our product or capabilities? Contact us, we are here to help!
Take a Tour
Take a tour of our solution to learn about Zerto’s features and benefits for yourself.
Try Zerto
Want to give Zerto a try? Get a free 14-day license or access to our on-demand labs.
RECOMMENDED CONTENT SEE ALL
Zerto Cyber Resilience Vault vs. Dell PowerProtect Cyber Recovery
As you consider a cyber resilience strategy for your assets, you need a clear understanding of your options. Check this comparison of Zerto
versus Dell and see the benefits you get when choosing Zerto.
ESG 2023 Ransomware Preparedness: Lighting the Way to Readiness and Mitigation
Enterprise Strategy Group conducted a survey of over 600 organizations to gain further insights into what proactive and reactive measures organizations have in place to defend against ransomware. Learn more!
Building a Cyber Resilience Vault with Zerto
Learn about Zerto’s vault architecture, combining Zerto’s ultra-low RPOs and RTOs with the untouchable performance of HPE Alletra and HPE ProLiant hardware, and enabling you to architect and customize an ironclad recovery vault.