
Enhancing Cybersecurity Resilience: Zerto’s Role in Supporting the Australian Essential Eight
In the ever-evolving landscape of cybersecurity threats, organizations globally are seeking robust solutions to protect their data. The Australian Signals Directorate (ASD) has developed a set of prioritized mitigation strategies known as the Essential Eight to safeguard internet-connected information technology networks. Let’s explore how Zerto, a Hewlett Packard Enterprise Company, and leading enterprise-scale solution, can help ensure your organization can align with the Essential Eight, providing enhanced protection against cyber threats.
Understanding the “Essential Eight”
The Essential Eight comprises crucial mitigation strategies, including patching applications and operating systems, implementing multi-factor authentication, restricting administrative privileges, employing application control, and ensuring regular backups. These strategies, outlined by the ASD, form a comprehensive framework to mitigate cybersecurity incidents effectively.
Zerto Is a Great Part of Your “Essential Eight” Strategy
Zerto empowers customers to run an always-on business by simplifying the replication, recovery, and mobility of on-premises and cloud applications. Zerto eliminates the risk and complexity of modernization and cloud adoption across private, public, and hybrid deployments. The simple, software-only solution uses continuous data protection (CDP) at scale to solve for ransomware resilience, disaster recovery, and multi-cloud mobility.
How Can Zerto Help Your Organization to Meet Elements of the “Essential Eight”
Here are few examples of how Zerto can help your organization meet critical elements of the Essential Eight.
1. Patch Testing for Applications & Operating Systems, with No Impact to Production
Zerto allows you to test your patch deployments with no impact on production, offering consistent validation of security posture. Easily spin up your environment or applications to create self-serve, high-fidelity clones that can be used for testing.
With legacy methods, patch testing and deployment are processes that fill IT professionals with fear and uncertainty. Even worse, these concerns cause many organizations to fall behind in their patching processes, ultimately leading to lost revenue due to regulatory violation fines—and that doesn’t even cover the security risks involved with irregular or late patches.
Zerto is the answer to any patch deployment hesitancies, offering easy, four-click initiation of non-disruptive testing against seconds-old, true copies of production in an isolated sandbox. After your four clicks, the testing can begin, providing you with visibility of the impact those patches will have on production. This allows you to stay compliant and limit potential exposure to threats while reducing the time it takes to get results and apply to production.
You can test patches your way with Zerto. The solution’s unique journaling replicates and backs up your data every few seconds without using the snapshot tools of legacy solutions.
This means that when it comes time to test patches, you work with copies that are true to production—not different environments with configuration drift that once resembled production—giving you complete confidence that everything will run as intended. Additionally, Zerto captures the state of all application dependencies with consistency down to the second, so you can test a complete application rather than analyzing one workload at a time.
The tests should run in their own isolated sandbox—without impacting production workloads, so you can perform them anytime. Other solutions require testing to occur at night or on weekends.
Background testing also enables near-zero RPOs and RTOs, empowering your teams to increase testing frequency.
2. Minimized Operational Impact: CDP Beats Regular Backups
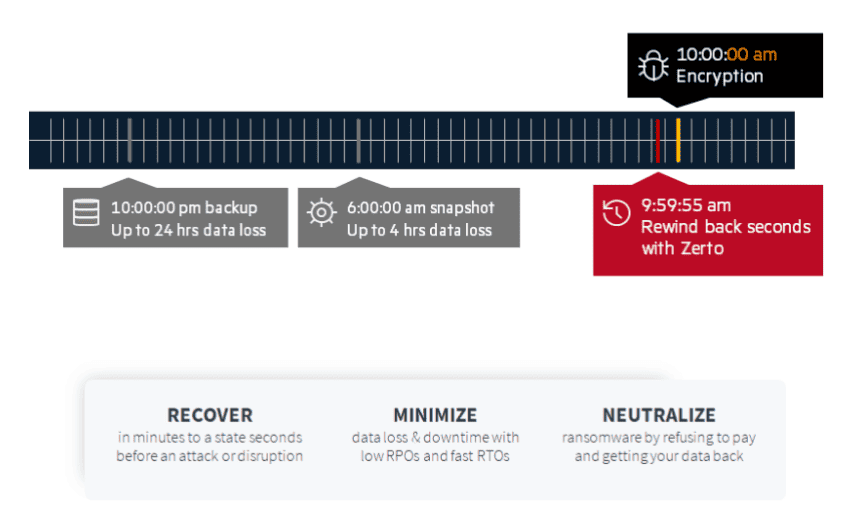
CDP, or continuous data protection, utilizes journal-based technology to keep a log of all the changes occurring in a specified time frame, offering any point-in-time recovery in increments of seconds for the entire length of the journal.
Unlike legacy systems, which accumulate data periodically throughout the day and then attempt to complete a backup during a time window, CDP constantly backs up your data. For example, snapshot-based recovery puts your business at risk of higher data loss due to infrequent restore points that are captured, while CDP minimizes this with thousands of restore points throughout the journal history.
CDP offers the insurance of minimal operational impact in the event of an outage—whether natural or man-made—and is, therefore, a great solution for disaster recovery and ransomware recovery use cases requiring the lowest downtime and data loss.
Zerto’s continuous data protection provides granular recovery of VMs to within seconds before data loss. The option to recover to many more granular points in time optimizes your RPO to seconds, dramatically reducing the impact of outages and disruptions to your organization.
3. Protection for Your SaaS Applications and Data
No matter which SaaS tool you are using, each recommend in their respective terms and conditions that customers use a third-party backup solution to retain the operational data and access they require in the event of an unforeseen disaster or disruption.
Zerto Backup for SaaS, powered by KeepIt, can provide regular isolated, tamper-proof backups for common SaaS applications such as Microsoft Office 365, Google Workspace, Zendesk, and more.
Zerto, Your Trusted Companion to Implement the “Essential Eight”
As organizations across Australia strive to implement the Essential Eight to bolster their cybersecurity posture, leveraging Zerto’s robust data replication, ransomware detection, application-centric protection, and automated failover capabilities, Zerto can play an enormous role in ensuring data availability and application integrity.
As a trusted solution used by major global players, Zerto is a testament to its effectiveness in safeguarding against modern cyber threats. Embracing Zerto alongside the Essential Eight can empower organizations to navigate the complexities of modernization and cloud adoption with confidence.
To learn more, visit our Zerto Overview page and see how Zerto can help your further. Our free on-demand labs are also an easy way to see and experience what Zerto can do for you.
For more specific questions, simply get in touch or request a demo.
 Anthony Dutra
Anthony Dutra 

