Real-Time Encryption Detection
A-to-Zerto Glossary of Terms
Overview
Ransomware detection has historically relied on approaches and methods whose challenges lies in keeping up with malware rapid evolution, achieving fast detection from the onset of an attack, and having these methods being decoupled from recovery. Real-time encryption detection, or real-time ransomware detection, can solve these challenges, and therefore contribute to an organization's cyber resilience by enabling fast response and recovery in the face of ransomware attacks.
Related Topics
What Is Real-Time Encryption for Ransomware?
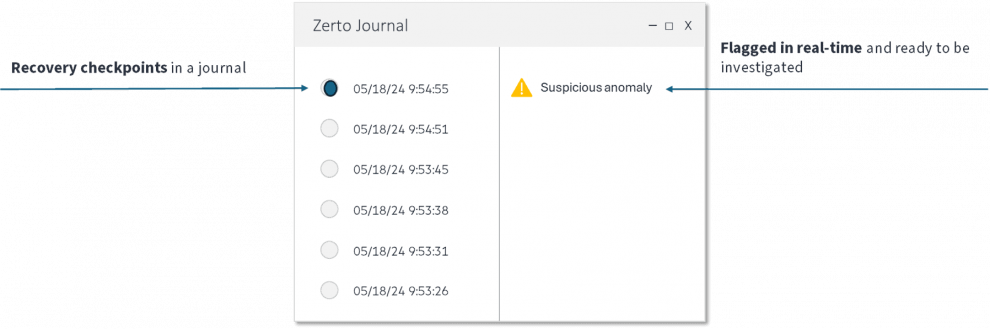
The key to achieving cyber resilience lies in the speed at which your systems can respond to ransomware threats. Early detection is paramount, as it enables prompt action. By harnessing advanced algorithmic intelligence for ransomware detection, you can receive alerts within seconds of detecting encryption anomalies, which often serve as early indicators of a ransomware attack in progress.
Figure 1: Example of real-time encryption detection using a journal
Why Use Real-Time Encryption Detection for Ransomware
Cyber threats are evolving rapidly, growing in complexity with advancements in encryption technologies. To combat this, it's crucial to deploy ransomware detection software capable of real-time encryption detection, alerting within seconds of an attack, and enabling a swift response.
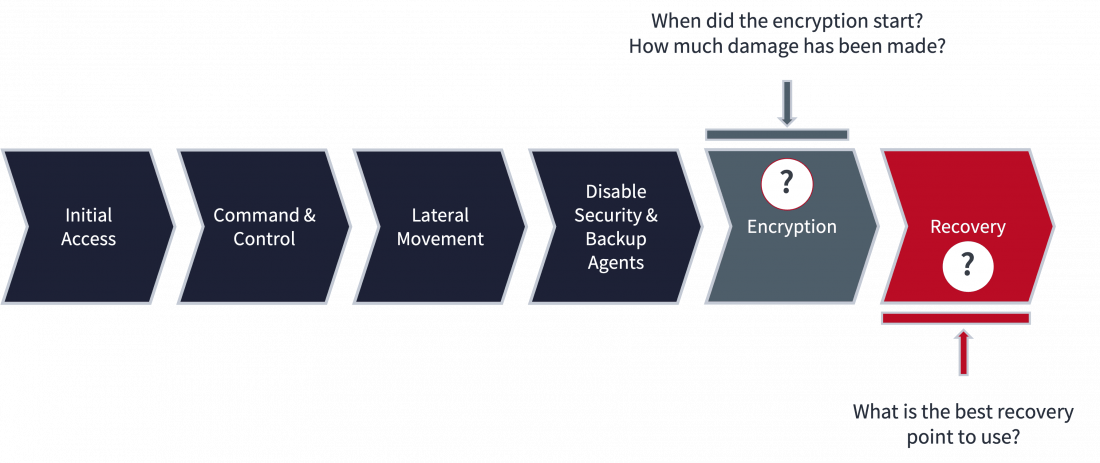
Figure 2: Anatomy of a ransomware attack
As shown in the figure above (figure 2:"anatomy of a ransomware attack"), the main two questions you want answers to are: When did the encryption start? How much damage has been made? What is the best recovery point to use?
Real-time encryption detection will help you to answer these questions.
Anatomy of a Ransomware Attack
Anatomy of a Ransomware Attack
To exit, click outside the video
Ransomware Attack Recovery: Rapid Response Is Paramount
The earlier you detect ransomware, the earlier you can take action to stop it and prevent data loss and downtime. This makes real-time encryption detection an indispensable tool in mitigating the ransomware threat once an attack has started. It will give you the closest point to the start of the encryption. From there, you might be able to assess the damage based on the time from that early detection point to when you can contain the attack.
Based on a Zerto analysis of globally diverse ransomware attacks to determine the median dataset size (183.5GB), and a study by Splunk¹ to get the average speed of ransomware encryption (20.96MB/s), real-time encryption detection could save the amount of data locked by a ransomware attack by 98.8%.
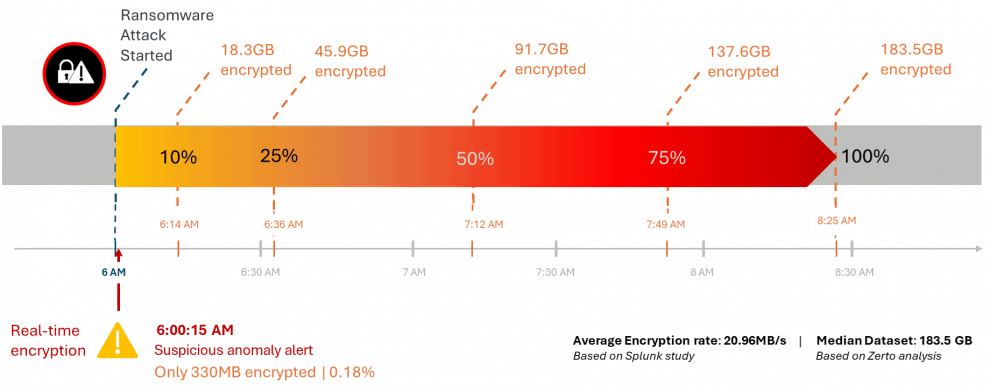
Figure 3: How much and how fast ransomware typically encrypts
As shown in the illustration above, the sooner you can detect, the sooner you can take action. That’s why real-time encryption detection has real-world ramifications.
Why Real-Time Encryption Detection Matters
Ransomware Recovery: Finding the Most Recent Clean Recovery Point Is Crucial
Real-time encryption detection also enables your security team to accurately determine the point of impact and therefore to know what data copies to use for your recovery. Restoring good, clean data, with the least amount of data loss, is essential to getting back to business as usual.
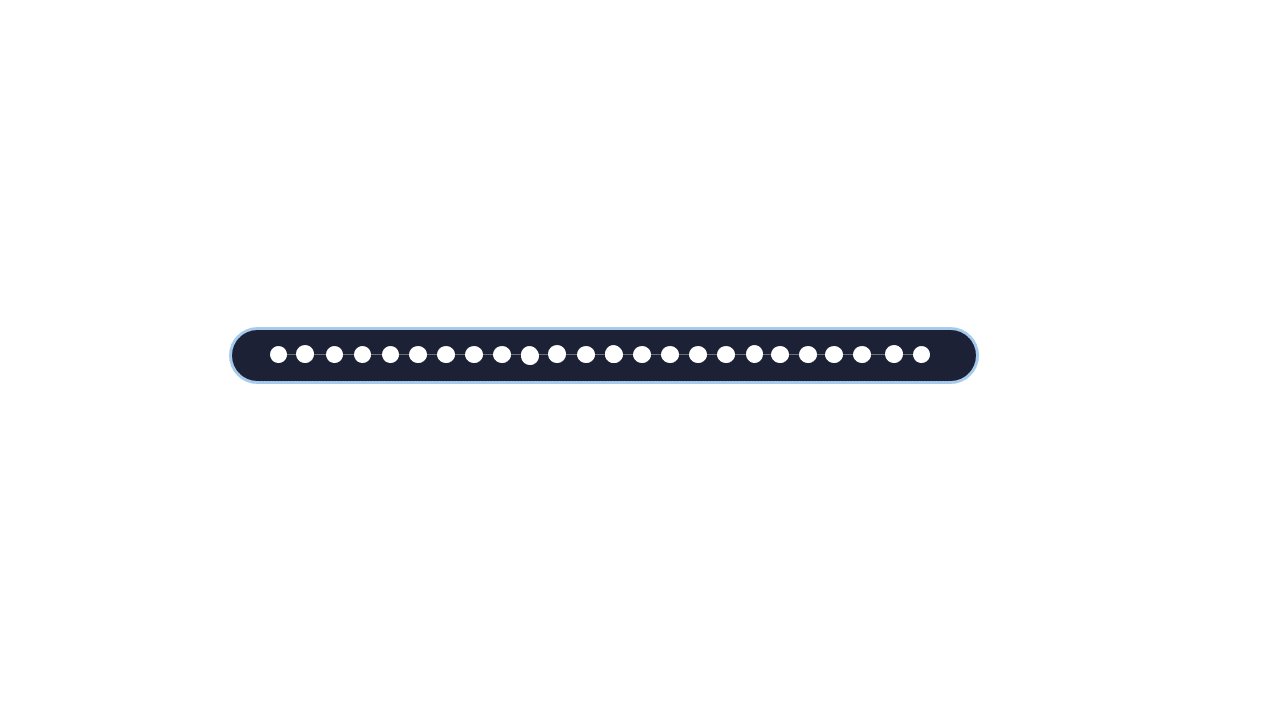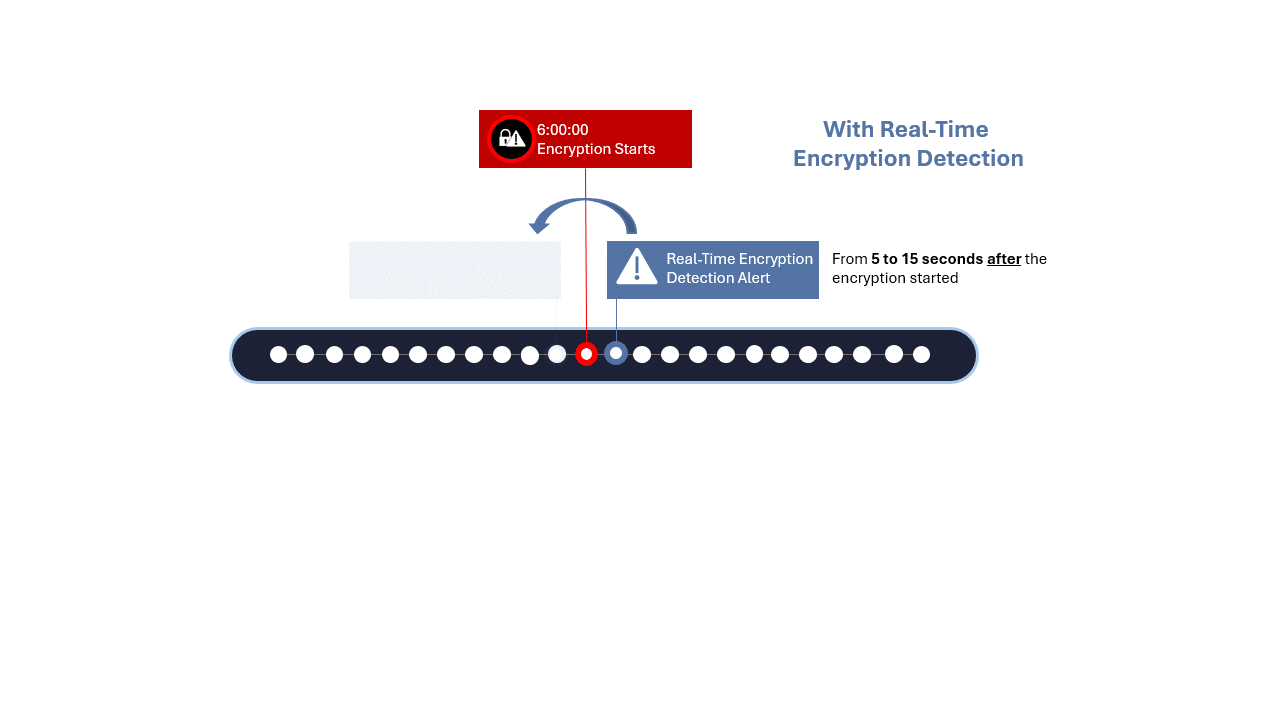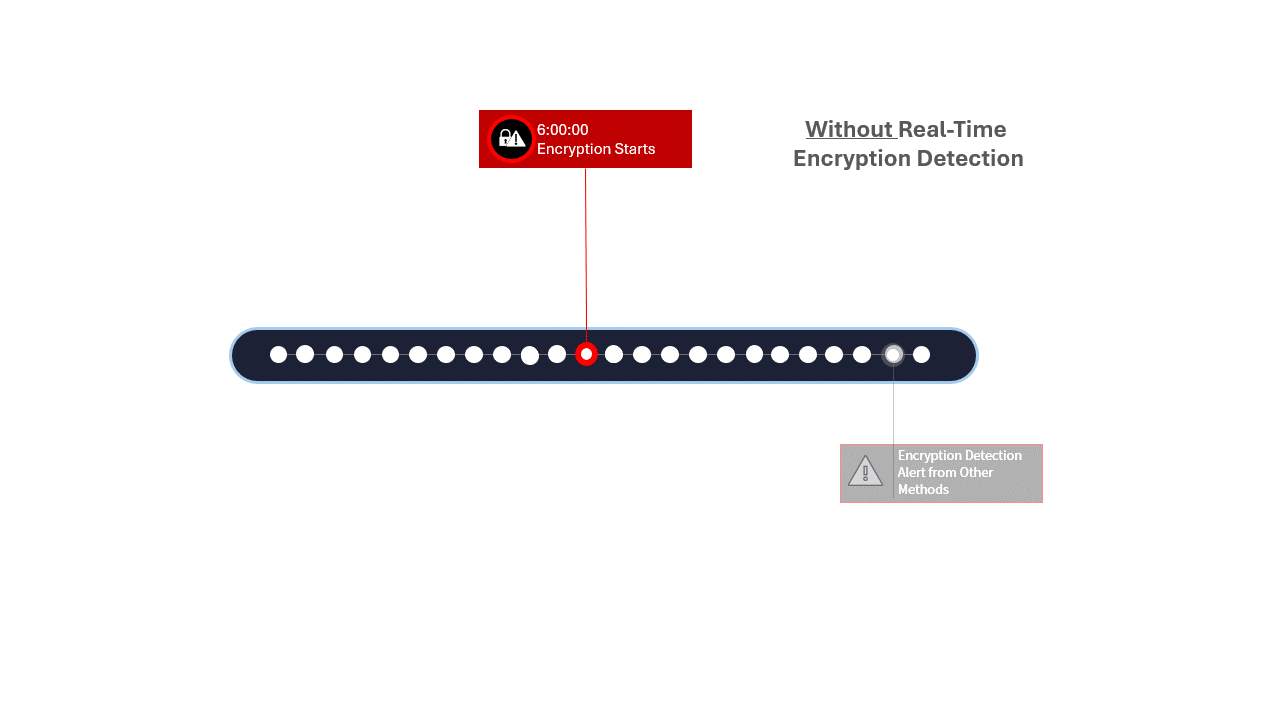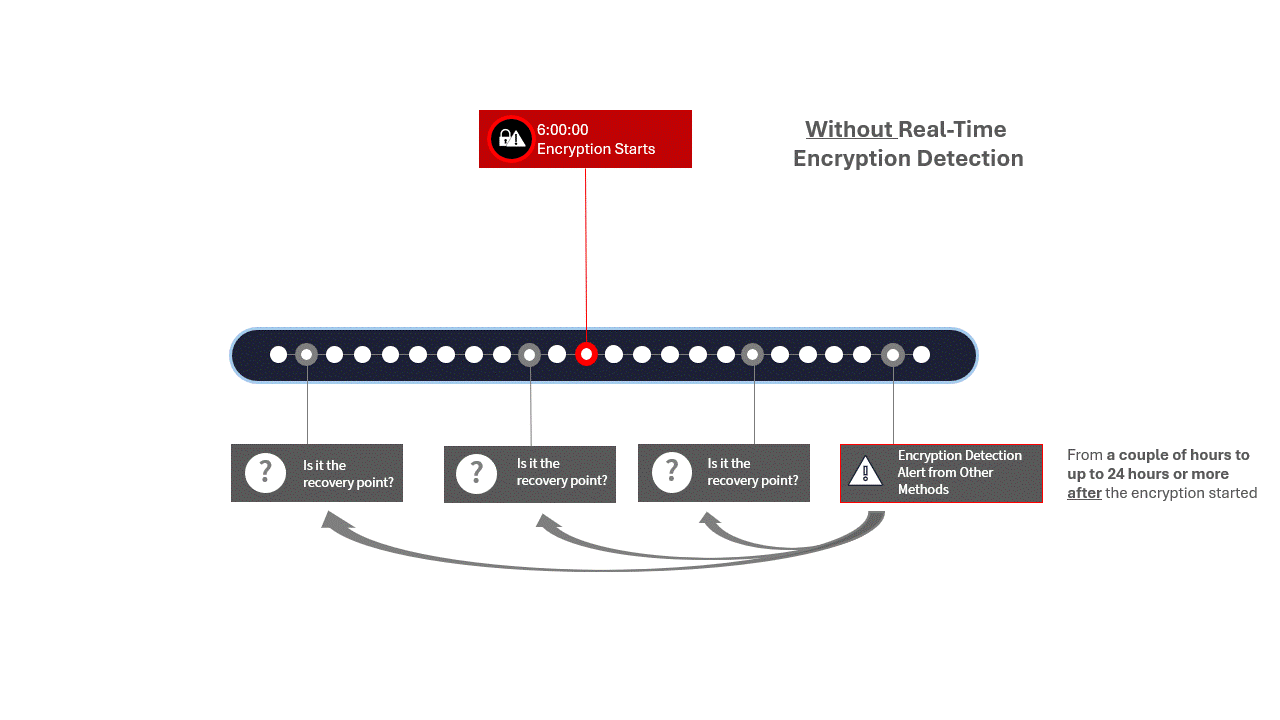
Figure 4: Animation comparing real-time detection to other periodic detection methods
The granularity of your recovery points will depend on the solution you use for getting your data copies. Granularity for traditional backup technologies may be up to 24 hours, for snapshots it can be 2 to 4 hours, whereas continuous data protection can deliver recovery points every 5 to 15 seconds apart.
Challenges of Periodic Ransomware Detection
Using early detection to protect your IT infrastructure against ransomware is much like guarding a bank vault. At a bank, there are security guards who periodically patrol the area and there are security cameras, which are periodically viewed to monitor suspicious activity. These typical prevention and response techniques are based on a periodic basis schedule which can provide some insight to a bank robber and sometimes mitigate a robbery.
Unfortunately, these periodic methods aren’t fast enough to keep up with the pace of today’s rapidly evolving security landscape.
Existing solutions typically scan backup copies, so the data is already hours old to start with (likely from last night’s backup job) and the malware scanning process itself takes quite a few hours added on top. It doesn’t mean that these methods should be eliminated, but rather that they should be complemented with other approaches.
In reality, to go back to the bank vault analogy, it would be ideal to detect the robber’s activity as soon as they enter the vault before they can steal anything. This is where early detection techniques come into play.
How to Detect Ransomware Attacks: Common Ransomware Detection Techniques
Ransomware detection sits between prevention and response—it’s the first line of defense. Since attackers use various evasion techniques to bypass detection, countering with multiple detection techniques is essential to identify ransomware before it damages your environment.
Here are several common detection techniques that can be used in combination to enhance the early detection effectiveness. Each detection technique’s pros and cons can be found in the blog post referenced below.
Direct Methods for Ransomware Detection
- Static file analysis: This method analyzes executable files for suspicious sequences of code without executing the code. .
- Common file extensions blacklist: This approach blacklists well-known ransomware extensions using file access monitoring tools. It is a signature-based approach.
- Honeypot deception techniques: The goal here is to lure attackers into unexpectedly revealing themselves. By setting traps, or “honeypots,” throughout IT environments, ransomware can be detected when attackers stumble into those traps. Rather than infecting or encrypting a real server, the ransomware instead will trip an alarm so immediate action can be taken.
- Dynamic monitoring of mass file operations: Here, the detection is based on monitoring the files system for mass file operations such as rename, write, or deleted within a specific time frame.
While still a foundational rule, the cyber-threat landscape continues to evolve and additional measures are necessary to fortify backup strategies.
Indirect Methods for Ransomware Detection
- Signatureless detection: This approach is anomaly- or pattern-based. It relies on a determined number of signals—often called indicators of compromise (IOCs)—that may mean malware is lurking or an attack is underway. It is called “indirect” because it does not involve the direct scanning of files to enable detection. IOCs can include suspicious elevation of privileges on a user account, sudden surge in CPU usage, deviations in I/O patterns or network traffic, anomalous encryptions events, and more.
These techniques have been mainly used and integrated into cybersecurity tools that attempt to prevent penetrations and attacks from occurring.
However, there is now an emerging option to add another layer to the multi-faceted defense strategy against ransomware: data protection such as backup and disaster recovery solutions. In this new added role, the main goal of these solutions is to detect a ransomware attack, and the sooner, the better.
Ransomware Detection Part 1: What is Ransomware Detection?
Data Protection Solutions Delivering Advanced Detection Features for Ransomware
Preventive cybersecurity tools can be excellent at detecting and stopping attacks, but ransomware can still break through despite all the barriers. Recovery solutions can be critical in these scenarios. They deal with the organization’s data and application for recovery purposes. Therefore, these solutions are well positioned to scrutinize this periodic or continuous stream of data and potentially detect ransomware attacks.
Here is below a list of some of these advanced detection features offered in data protection solutions:
- Real-time monitoring and behavior analysis: This works by analyzing block patterns and behaviors from streamed data, as they are replicated.
- Machine learning (ML) and artificial intelligence (AI): This leverages ML and AI to analyze vast amounts of data, recognize ransomware patterns, and generate predictive models that can identify new strains of malware.
- Heuristic analysis and signature-based detection: This method examines the behavior of files and programs to identify potential ransomware.
- Integration with threat intelligence: The goal here is to leverage the wealth of information from threat intelligence platforms to proactively identify and respond to new ransomware threats.
- Automated incident response: Automated incident response mechanisms are used to immediately isolate infected systems and trigger response actions.
- Continuous monitoring and auditing: By monitoring logs, user activities, and system behavior, businesses can proactively identify any potential vulnerabilities or signs of compromise
Ransomware Detection Part 2: How Data Protection Drives Resilience
Zerto Continuous Data Protection Delivers Continuous Detection for Ransomware Encryption
Zerto’s software-only solution applies algorithmic intelligence to its real-time encryption detection, significantly reducing the scale or blast radius of a ransomware attack by alerting you within seconds. By eliminating the need to wait hours or days to assess the situation, you can drastically minimize data loss and expedite the recovery process.
Zerto leverages its proprietary continuous data protection to apply the Zerto Encryption Analyzer on the stream of data being replicated. As a result, Zerto’s detection is real-time and always-on.
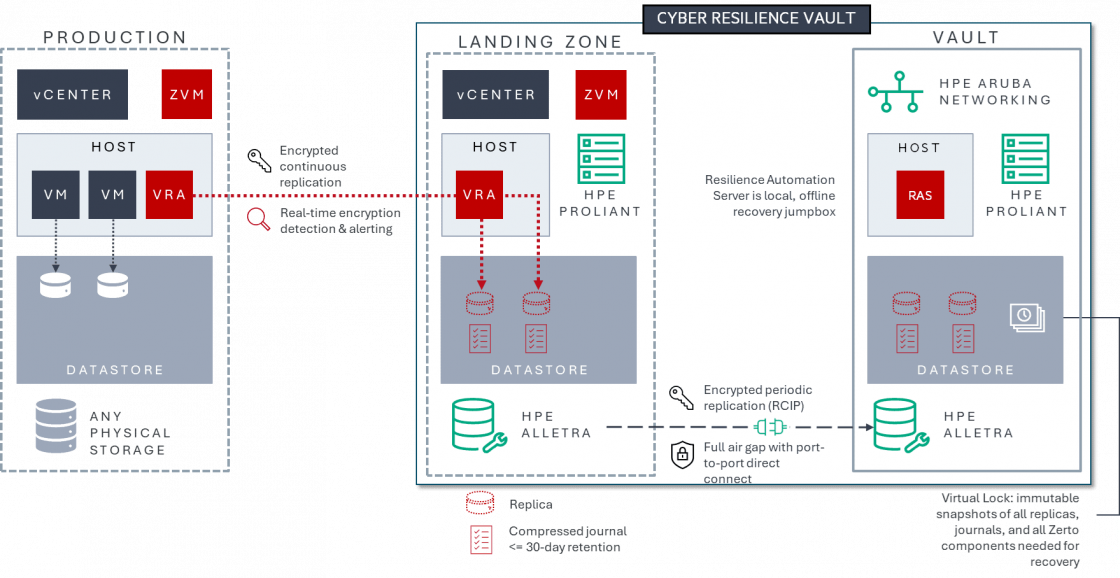
Zerto's real-time encryption detection is also used in the Zerto Cyber Resilience Vault.
Understanding Real-Time Encryption Detection with Zerto
Zerto Cyber Resilience Vault
Frequently Asked Questions
What is the difference between signature-based and signatureless ransomware detection methods?
Signature-based methods uses malware definitions to scan for known variants. They have the advantage of generating relatively few false positives—since this approach is not based on inference, confidence levels can be high when a variant is detected. The downside is that a library of ransomware definitions must be created and kept up to date. As malware evolves, it can be challenging to keep up; by its very definition, this approach is always playing catch-up to threat actors.
Signatureless methods are anomaly- or pattern-based. They rely on any number of signals—often called indicators of compromise (IOCs)— that may mean a cyberattack is underway. The signals used can greatly vary depending on the vendor and solution. Examples include: unexpected logins from an unusual geography, suspicious changes of privileges on a master account, anomalous encryption events, and more.
The breadth and variety of IOCs makes anomaly detection a popular approach. Many of the vendors developing these solutions are purpose-built data security or cybersecurity companies who can detect ransomware quickly and with high degrees of confidence.
Why are data protection solutions focusing on ransomware detection?
While cybersecurity tools are very good at detecting and stopping attacks, bad actors keep improving their ransomware capabilities to break through these more and more sophisticated barriers.
And if an attack goes through, what’s next? On top of containing the attack, recovery activities need to take place as soon as possible. But how do you know what data to restore: which recovery points are clean and unencrypted, and which are compromised?
These cybersecurity tools, however strong they are, are therefore decoupled from recovery. And this is what is driving data protection solutions that specialize in recovery to focus on ransomware detection capabilities.
How does the real-time encryption detection in Zerto work?
Zerto, and its Zerto Encryption Analyzer, is built on a foundation of continuous data protection (CDP), a technology widely considered to be the best way to reduce data loss and downtime.
The proprietary CDP engine in Zerto has been battle-tested and proven at scale, resulting in thousands of customers achieving RPOs of seconds whether protecting 70 or 700 VMs—or even 7,000 VMs simultaneously.
Zerto’s software-only solution applies algorithmic intelligence to alert you within seconds when there’s an encryption anomaly that could signal the start of ransomware’s detonation phase.
What are the benefits of encryption detection through Zerto?
Zerto CDP is essential to recovery, but this foundation of block-based (not file-based), hypervisor-level replication unlocks five primary benefits for encryption detection as well, including:
- Real-time: The always-on, near-synchronous replication engine in Zerto unlocks the ability to analyze data on a virtually real-time basis with high degrees of granularity.
- Agnostic: Zerto is completely indifferent to the type of file being encrypted.
- Relative: The Zerto Encryption Analyzer is dynamically adaptive—it does not make assumptions about the digital estate and does not need manual updating based on new or different environmental variables.
- Agentless: Zerto does not use any agents on protected VMs, eliminating the opportunity for threat actors to disable or to hijack these agents.
- Lightweight and non-disruptive: There are no additional components to deploy and configure—Zerto uses the existing Virtual Replication Appliances (VRAs) and Zerto Virtual Managers (ZVMs) that are required for normal CDP and are already lightweight. And the encryption analyses do not interfere with the replication process.
What is the ransomware detection method Zerto uses?
Zerto’s encryption analyzer uses a signatureless approach to detect encryption. It assesses data patterns and analyzes entropy to detect unusual encryption that may indicate the locking phase of a ransomware attack has begun. However, unlike other vendors using this approach—which are usually purpose-built data security or cybersecurity vendors—Zerto’s real-time detection is coupled with recovery.
What are other ransomware detection differentiators in Zerto?
Zerto’s real-time encryption detection comes at no additional cost: it is included out of the box. So, there are no paid add-ons, and no extra subscription to pay for. You simply get more out your data protection solution at no extra cost.
Zerto also maximizes your operational efficiencies in two ways. First, there is no additional software to install, configure, and manage. Second, it unifies the efforts of security and infrastructure teams through the fast detection of a ransomware attack and the subsequent and enabled swift recovery.
Finally, with Zerto you get accelerated time to greater value from your solution. As a no-added-cost complement to your current security stack with its detection capabilities, you can start detecting anomalies at the same time you start protecting your data.
Other Resources
LATEST FROM ZERTO SEE ALL
Real-Time Encryption Detection
Explore Zerto resources related to real-time encryption detection.
Take the Stress Out of Ransomware Recovery
Dramatically mitigate the risks and impact of cyberattacks by having the right ransomware strategy in place.
Essential Guide: Ransomware Recovery
From the definition of ransomware, description of how a ransomware attack unfolds, right down to cyber resilience and ransomware recovery, we cover everything in this ultimate guide.
What is Zerto?
Learn about Zerto and how it can help you solve your data protection and recovery challenges.
1. Splunk: An Empirically Comparative Analysis of Ransomware Binaries: - https://www.splunk.com/en_us/form/an-empirically-comparative-analysis-of-ransomware-binaries.html