Risk Management Process- Part 1: Overview
Risk management describes how a business identifies, analyzes, and responds to threats and risk factors that impact its profitability, viability, and strategic goals. These threats are varied and include emergencies, natural disasters, IT and technological issues, legal and regulatory problems, and financial uncertainties. Risk management attempts to control future threats by planning preemptively and deploying effective risk-control measures.
In this miniseries, we are going to follow the entire risk management process, focusing on its application to operational risks. We will discuss risk management, the critical importance of business impact analysis (BIA), and the essential steps involved in a thorough risk assessment. We will end the series with an overview of the risk prioritization and mitigation stages of the process. This series will provide insights to help you ensure you are successfully navigating risk and that your organization is prepared to resume optimal operations after a disruption.
Overview of Risk Management for Operational Risks
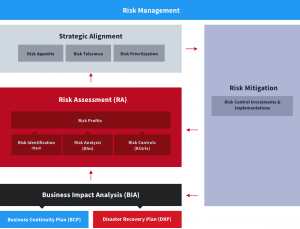
The risk management process is continuous. It involves both top-down and bottom-up approaches that feed on each other so a business is able to achieve its goals in what it considers a safe way. At the top, executives set and state the organization’s risk appetite. Downstream, teams use this input to ensure that registered risks establish appropriate controls to keep their residual risk levels below risk tolerance thresholds. At the bottom, teams continuously evaluate their operating environment, identify potential new risks, assess them, and potentially bring them upstream to raise awareness and get funding to implement new controls. This is a simplified overview of the risk management process.
Process Pre-requisites
Prior to starting the process, it is crucial to have the risk universe defined and the level of risk that is acceptable to your organization specified—in other words, begin with the end in mind. To determine your organization’s risk appetite (the amount of risk it is willing to accept to realize its objectives), you need consensus from leadership and all stakeholders. This ensures your risk management framework will prioritize mitigation strategies and best practices for enterprise risk management.
The aim of this framework isn’t to eliminate all risk but to ensure that the organization makes smart risk decisions that retain and increase enterprise value. This framework captures your business continuity and disaster recovery plans, so it must be regularly updated as the organization scales and its risk profile expands or shrinks.
The other key prerequisite is a solid governance framework. It’s essential for decision-making, as well as managing the entire risk process.
Process Initial Cycle
An organization formalizing its risk management process for the first time would typically start with BIA, then conduct an in-depth risk assessment, which results in risk prioritization against the organization’s risk appetite and, ultimately, in investments in adequate mitigation options. Those mitigation strategies and implementation would in turn affect the initial BIA, and the organization’s risk profile would have to be updated to reflect this evolution.
Post-initial Cycles
Once the initial cycle is completed, there are no starting and end steps within that process. Changes at any level—affecting either business strategy or environment—trigger activities across all stages and establish a new baseline. Even though regular risk assessment reviews might be scheduled, significant business changes should trigger an immediate response.
Risk Management Process Step by Step
Let’s explore each one of these steps in detail to better describe the risk management process for operational risks in its initial cycle.
Step 1: Perform a Business Impact Analysis
A BIA outlines the potential consequences of risks and disruptions on critical functions and business processes. A BIA provides business leaders with valuable information they need to develop contingency plans and informs intelligent risk prevention, mitigation, and recovery strategies. It also forms the basis for investing in risk management strategies, such as business continuity and disaster recovery.
Essentially, a BIA is a formal assessment of risk events to identify potential loss scenarios, such as:
- Delays in implementing business expansion plans
- Customer dissatisfaction
- Contractual penalties
- Regulatory fines
- Increased expenses
- Lost sales and income
BIA is also essential because it highlights the business continuity SLAs for critical functions and business processes. These are used to determine the recovery point objectives (RPO) and recovery time objectives (RTO) used in disaster recovery.
Step 2: Complete Your Risk Assessment
This is one of the most important stages in the risk management process. A risk assessment systematically evaluates the risks and potential threats that could negatively impact your business operations, and includes the following steps:
Step 2-1: Risk identification—This outlines the risk types and emergency scenarios that could negatively or positively impact your organization’s operational capability.
Step 2-2: Risk analysis—This determines the likelihood and impact of individual risk types. An earthquake is an example of a low-probability event, while an employee calling in sick is a high-probability event. However, the earthquake is a high-impact event, and a sick employee will have significantly less impact on company operations. The BIA, if already completed, determines impact.
Step 2-3: Risk controls—After establishing the impact and likelihood of individual risk types, your next step identifies risk controls to eliminate or mitigate the risk impact. Some risks will be within your organization’s risk appetite. Such risks require no additional actions or control measures before they are acceptable.
For risks that fall outside this category, business leaders can deploy several risk control measures such as diversification, purchasing insurance, upgrading IT equipment, training employees, designing effective systems, and deploying security measures, among others.
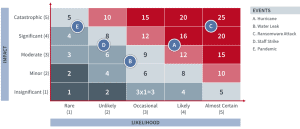
Step 2-4: Risk profile and risk map—A risk map is a visual representation of an organization’s risk profile and is the result of the risk assessment steps—risk identification, analysis, and controls.
The risk map enables you to visualize the likelihood, impact, and relative importance of each risk and identify intersecting points or overlapping areas of interest. It also shows how all organizational risks rank in likelihood and potential. These are ranked by assigning qualitative, quantitative, or semi-quantitative scores to each risk.
Usually, organizations create several risk maps based on the area of focus—considering operational, strategic, financial, or governance and compliance risks—to create a composite risk profile.
Organizations consolidate these profiles to provide an organization-wide, comprehensive risk profile. Executives use this profile to understand the most critical risks faced by the organization and decide where to invest or obtain resources to address these risks, based on the risk appetite and tolerance of the organization, as shown in figure 2.
Step 3: Achieve Strategic Alignment, from Risk Appetite to Risk Prioritization
The more impactful a risk is, the higher its priority.
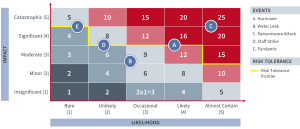
Essentially, risk prioritization leverages the risk map to rank risks in order of priority and severity. It is also a function of the risk appetite and risk tolerance set by the organization. Once it is integrated into the organization’s risk profile, it may modify what risks need to be prioritized.
After consulting with stakeholders, business leaders outline the organization’s risk appetite and tolerance. This decision is influenced by business objectives, regulatory legislation, company culture, and political environment.
Risks with high probability and high severity of impact will most likely top the list, while those with little or no significant impact can be close to the bottom. But risks between these extremes may or may not be considered critical, depending on how they rank in the organization’s risk tolerance.
Organizations can use a risk map that incorporates levels of risk tolerance to create a risk ranking and ensure strategic alignment between risk management and business goals.
Step 4: Mitigate Risk
After carefully considering a prioritized list of risks, businesses can explore cost-effective risk mitigation strategies and controls to achieve an acceptable level of risk. If the mitigation strategies can’t reduce the impact of a risk to within acceptable limits, the organization must take steps to either eliminate its exposure to the risk scenario or accept the risk.
Adjust Risk Profile, Risk Map, and BIA
Enterprise risk management is an iterative process. As business leaders implement risk mitigation strategies, they should analyze the results and refine their strategies for the next iteration. When a risk control measure successfully eliminates or mitigates an operational risk, you should review and update your risk assessment reports.
When necessary, you can use the updated reports to refresh your BIA and risk maps so they reflect your current risk profile. Since the BIA is used to create business continuity plans, SLAs, and disaster recovery plans, as well as designate RTOs and RPOs, you also need to review and update these documents.
Review and Monitor Risks and Related Plans on a Regular Basis
Scheduling regular risk assessment reviews is a critical step that helps ensure the success of the risk management process. Business leaders need to track and monitor their risk management efforts to ensure that risks remain within acceptable limits. Significant shifts in regulatory terrain, customer demand, technological changes, the competitive landscape, potential hazards, and stakeholders’ preferences can occur at any time in a modern business environment.
These shifts can affect an organization’s risk appetite and tolerance. Regularly reviewing and updating risk assessment strategies in line with evolving risk profiles helps organizations stay on top of emerging hazards and ensures continuous alignment between risk posture and business goals.
Risk Management Is Part of a Continuous, Never-Ending Cycle
An effective risk management process is built on a solid understanding of an organization’s risk appetite, business goals, and its unique operational landscape. Since these factors do change from time to time, an organization’s capacity to successfully navigate risk depends on its ability to react and respond to evolving factors that affect its risk profile. Therefore, risk management is a continuous, never-ending cycle—aimed at optimizing and aligning an organization’s risk appetite and risk tolerance with its strategic business goals.
This is where a thorough business impact analysis comes in handy. A BIA report helps business leaders keep risk factors within acceptable boundaries by highlighting high-impact risks and their potential impact on assets and operations.
To help organizations get started, we’ll explore the BIA process in the next part of our miniseries.