Ransomware cyberattacks are everywhere in the news: In Taiwan, major gas stations were unable to process payments. Increasingly targeted during the current pandemic, hospitals and medical facilities have been forced to turn away patients. Banks were unable to make foreign currency conversions. Dozens of city governments have been crippled. Many small businesses have been forced to close.
Hackers have been ruthless with their malicious malware attacks, exploiting users from small business to global enterprise organizations, both private and government.
The Challenges
Just in 2019, ransomware threats increased by 300%—and not only are attacks growing more frequent, but they are much more costly to recover from as well. The total estimated cost of ransomware attacks for 2019 was $11.5 billion, with an average recovery cost of $1.4 million per attack for an individual organization.
A successful cyberattack can bring your operations to a stop, potentially for days, weeks, or even permanently. Without the right plan and solution, data recovery efforts can leave gaps in data, become time-consuming, labor-intensive and costly. And even if you do recover your data, damage to your reputation can be lasting, causing customer attrition or brand avoidance. These costs, along with potential ransom costs, can cripple a business.
Cybersecurity: The First Line of Defense
As hackers become more sophisticated and attacks to IT systems become more common, the reality is that it’s not a matter of if you will be targeted by a cyberattack, but when. While you won’t be able to stop all attacks, creating a comprehensive cybersecurity and disaster recovery plan is paramount to minimizing your risk.
That was the intention behind the Cybersecurity Framework launched by the U.S. Commerce Department’s National Institute of Standards and Technology (NIST). This flexible framework helps organizations understand the best practices they should use to manage their cybersecurity-related risk, centered on these core functions:
- Identify
- Protect
- Detect
- Respond
- Recover
NIST identified these functions because they are “the five primary pillars for a successful and holistic cybersecurity program. They aid organizations in easily expressing their management of cybersecurity risk at a high level and enabling risk management decisions.”
Recovering from Ransomware with Cyber Resilience
Many organizations do a good job with the first four pillars, yet when malware makes it through their defenses they struggle with recovery. But this final step has become more critical than ever before. Having to restore to a day-old or even week-old backup means data loss and increased time and expense in recovery efforts. You can’t afford that kind of a non-resilient solution.
Continuous Data Protection is Key
The key is having a solution that’s always on, with enough granularity to recover to a point in time precisely before the attack occurred, without time gaps. Zerto’s IT Resilience Platform™ uses Continuous Data Protection and keeps your data protected in real time. In only a few clicks, your data is recovered in seconds. Additionally, our journal-based recovery is flexible enough to recover only what you need: be it a few files, virtual machines, or an entire application stack.
To recover to the exact point before an attack, you must be able to pinpoint exactly when the attack occurred. With Zerto Analytics and the Zerto Virtual Manager, you can use network, journal, and IOPS statistics to determine the precise moment the ransomware became active and recover to within seconds before it. Zerto also allows you to quickly perform a failover test to see if you have the right point in time. If not, you can easily failover again to a different point—all with minimal effort and recovery time.
A Tale of Two Ransomware Attacks
Take, for example, TenCate, a multinational textiles company, who experienced ransomware attacks twice: the first before implementing Zerto and the second after implementation. Their experience recovering from ransomware in these two experiences reveals the power of Zerto’s IT Resilience Platform™.
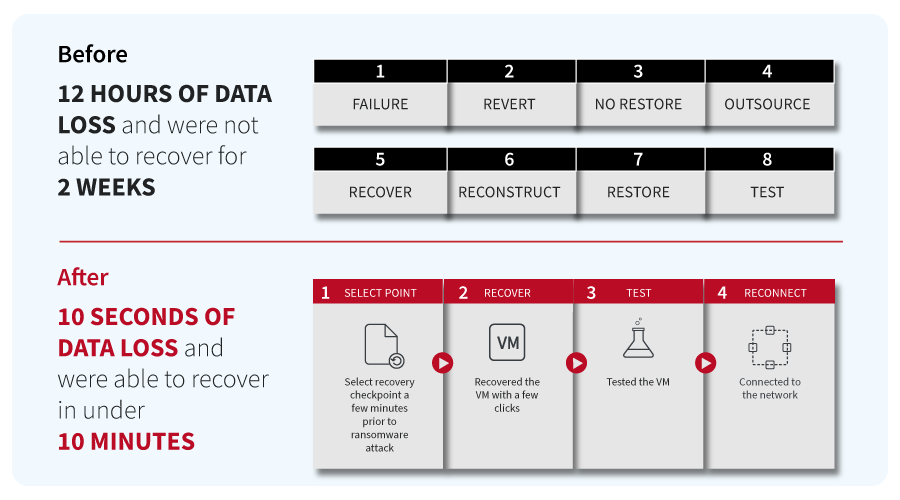
In the first attack, one of TenCate’s manufacturing facilities was hit with CryptoLocker, and all file servers were infected. TenCate’s used traditional disk recovery, experiencing 12 hours of data loss, and they were not able to recover for two weeks.
After implementing Zerto, directories on a file server were hit by a more advanced form of CryptoLocker. This time, TenCate only experienced 10 seconds of data loss and were able to recover in under 10 minutes.
Going Beyond Surviving Cyberattacks
The Zerto IT Resilience Platform™ is the next evolution of disaster recovery. With always-on hypervisor-based data replication and recovery granularity within seconds, Zerto gives you the utmost confidence in your recovery plan, even when ransomware or other cyberattacks do get through.
Watch this video below to see how to quickly recover from ransomware and other threats with Zerto, and download the Cyber Attack Survival Kit to learn more about cyber resilience and how Zerto can help you mitigate the risk of downtime and data loss due to a cyberattack like Ransomware.