Complete Data Protection Using Zerto
What does complete data protection mean?
Data protection is generally associated with things such as Array Based Snapshots (ABS), VMware/Hyper-V Snapshots and backup software. In each of the above cases there are many variables that need to be considered when choosing the appropriate technology for the appropriate use case with two of the most important being the Recovery Time Objective (RTO) and the Recovery Point Objective (RPO).
So, let’s use these two variables to determine the right technology. If we are protecting Virtual Machines (VMs) we could use either ABS or virtual snapshots, however with these technologies, the RTO could be multiple minutes through to multiple hours, not to mention the impact on the array and the other VMs in the environment, as we are snapshotting Logical Unit Numbers (LUNs) we are generally snapshotting and moving more data than what we actually need to protect the selected VMs. This is due to what I call VM sprawl, the initial VM datastore has been filled up and a new one has been added. This occurs every time there is growth or when new storage is added to the environment. At this point, unless you‘re very vigilant, VMs are placed across multiple datastores.
Let’s now look at using backup software. Here we have two ways to achieve data protection. The first, is to leverage the ABS or virtual snapshots and have the backup software catalogue the backups. Again, we are still limited to the same RTOs as before with the same extra overhead due to VM sprawl. The second is to install a backup agent. This could be disruptive process to the VM as some agents require a reboot to install the backup software drivers Here also from an RPO perspective we can get better RPOs, however this is achieved by needing to have an initial full backup then you are able to protect the subsequent changes since the first full backup and we will need a backup window of at least 12 hours. Not really a good place to be if you’ve had data corruption or been hit by a CrypoLocker Virus. We now need to consider the RTO, how long will it take to recover the initial full backup and then apply all the changes since that first full. It could take hours to recover and replay all the changes. This is based on the assumption that the data is recoverable and when was the last time you did a recovery to validate the backups. Not a good place to be when the pressure is on!
In all of this we haven’t even considered the data protection of applications running in the cloud. The standard protection methods do not apply, thus you will need to have a different process to protect your data in the cloud.
What if we were able to achieve RPOs of seconds and RTOs of minutes regardless of where the workload was without impacting the VM and without the need to install an agent within the VM. Yes, this is achievable using Zerto’s Virtual Replication (ZVR).
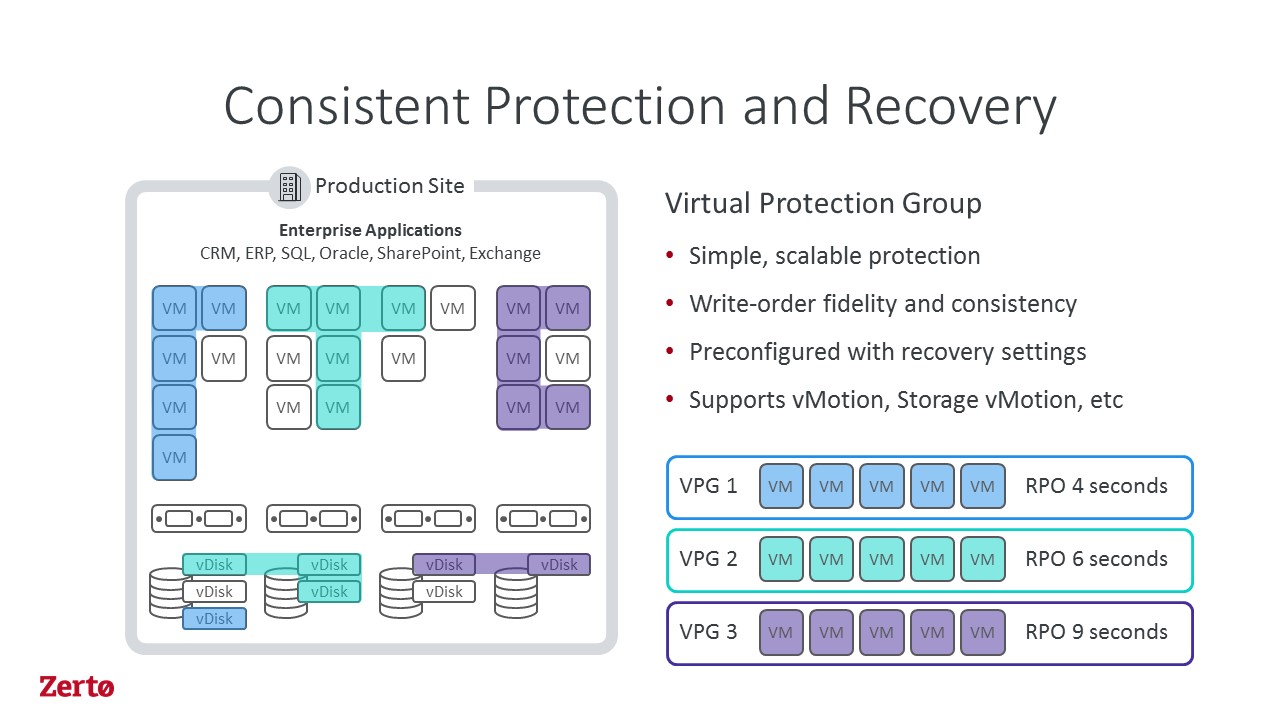
Zerto’s Virtual Replication (ZVR) gives you the ability to protect your workloads as applications rather than just individual VMs, add to this the ability to recover a single file or folders without the need to boot the VM.
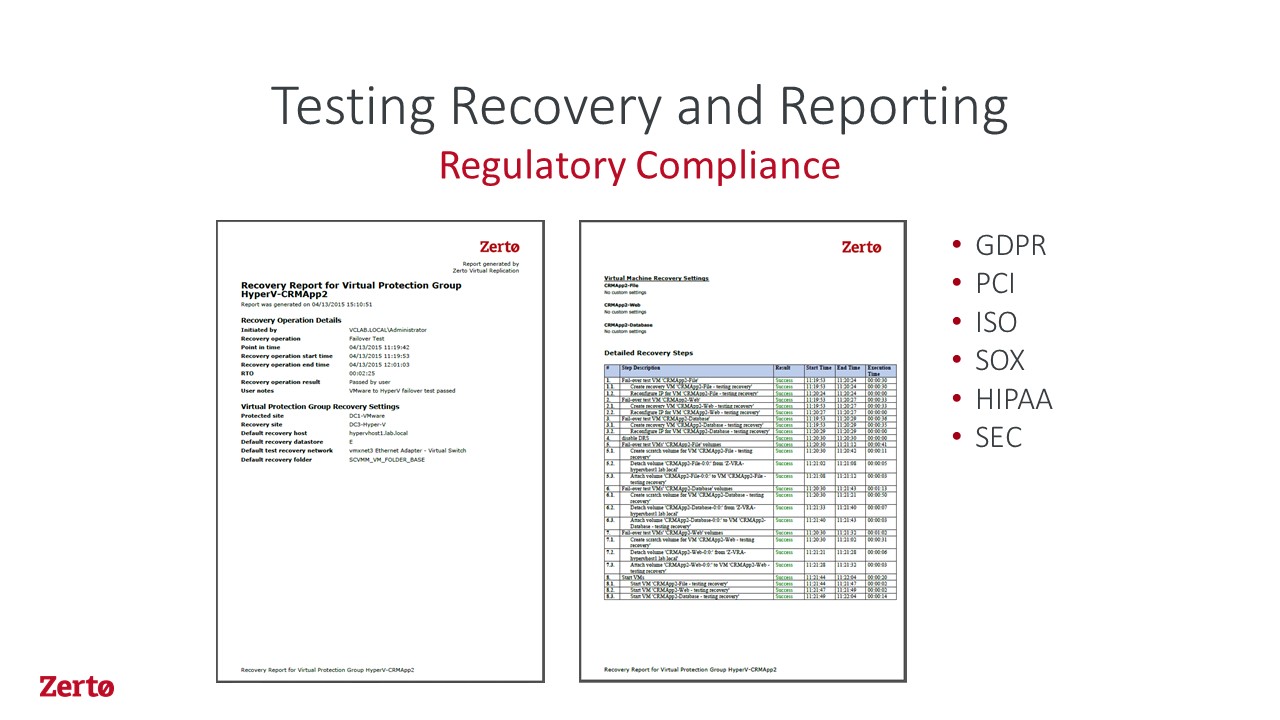
This now changes the whole data protection discussion as we can apply this same level of protection and resiliency across all your workloads regardless of where they are, on premise or in the cloud. Couple this with the ability to test and validate your protected application as often as you like without disrupting production. In fact, what if you could do a disaster recovery test to show the business that when the time comes you can provide recoverability and document the proof, satisfying all of the major compliance regulations. Zerto’s Virtual Replication (ZVR) can also satisfy your long-term data protection requirements, again without impacting production, by making full backup copies of the VMs on the Disaster Recovery (DR) side.
Zerto’s Virtual Replication (ZVR) provides you a complete data protection solution that allows you a standard protection method for all your business-critical applications regardless of where they are running, with the knowledge that you can test and validate your data protection.